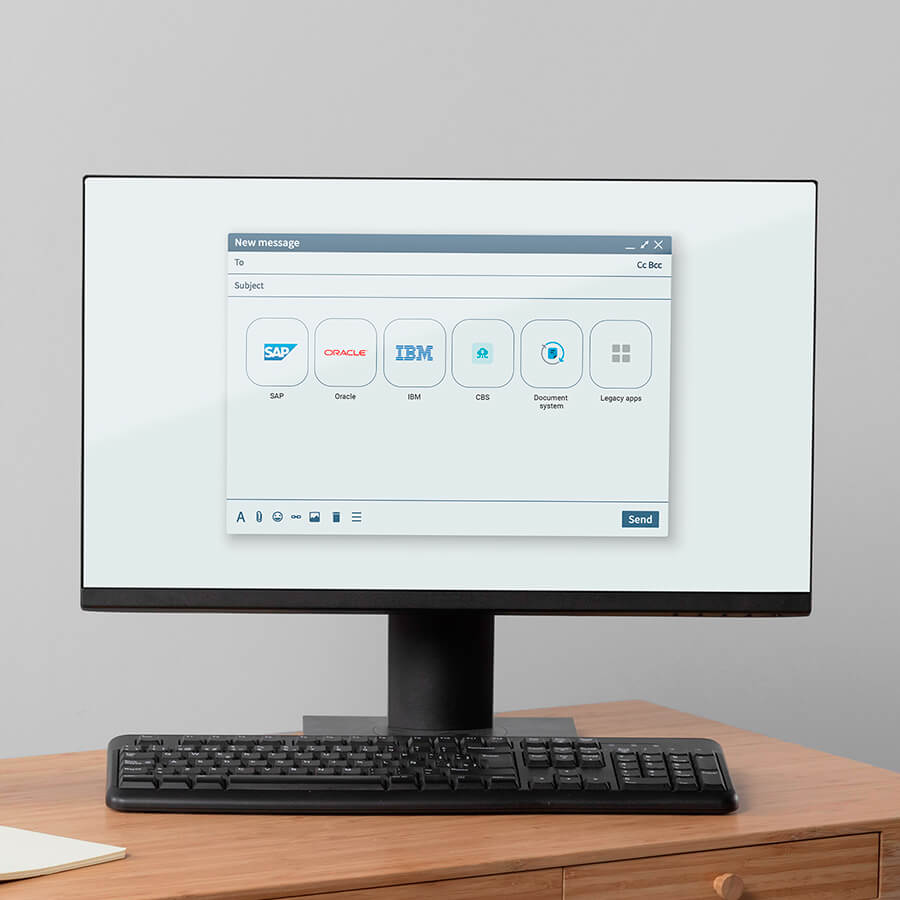
Companies from all industries and sectors largely rely on a wide spectrum of desktop and web applications, including both general-purpose and specialized software.
General-purpose software is widely used in the Electronic Document Management Systems (EDMS), Enterprise Resource Planning (ERP) Systems, and accounting systems. On the other hand, specialized applications often serve as software components for Automated Process Control Systems (APCS), Customer Relationship Management (CRM) and Warehouse Management Systems (WMS). That said, specialized applications are often custom-made.
All these services can be used for addressing a variety of corporate tasks — offering government services, ensuring legal compliance, or engaging in revenue-generating activities. Most of such systems require authorization.
It is important to keep in mind that some software solutions cannot be easily integrated with a domain directory service such as Active Directory. Many services also maintain internal user databases, and therefore require separate authentication. Sadly enough, applications that support sign-on options other than password-based authentication are still uncommon.
That said, password-based authentication has several widely known disadvantages:
- You need a security incident to actually occur to learn that your password has been compromised, while intruders will do their best to disguise their presence in your IT infrastructure.
- The risk of theft and illegal use of passwords for malicious activity intensifies in the case of remote work.
- Passwords are highly vulnerable to social engineering techniques when users are coerced to directly or indirectly disclose their password to the intruder.
- Regular users may find it hard to meet all password security requirements, especially when they have to use separate user accounts for different services.
Given the prevalence of broadband Internet access and the growing popularity of remote connections, these disadvantages may become a critical vulnerability for both your corporate applications and the entire company. After all, if the credentials of one of your accountants were to fall into the hands of intruders, this may have quite serious implications for your company, including total shutdown of its operations.
The choice of desktop and web applications may be enormous, even if we talk about one single industry, which makes the development of individual connectors (special modules enabling pass-through authentication) for each target app extremely challenging. This is not an easy task even when it comes to most popular services. Likewise, the development of connectors for your custom applications may prove quite expensive; not many companies can afford this.
Different kinds of software implementing Single Sign-On technology are widely used for ensuring secure unified authentication across all corporate desktop and web applications. Products of this class are also designed to build centralized authentication and password management systems (its functionality being similar to Password Manager software).