The Axidian Privilege software suite has been updated to Version 2.6. The release includes a lot of improvements and a number of new features that make activity log analysis easier and improve account management.
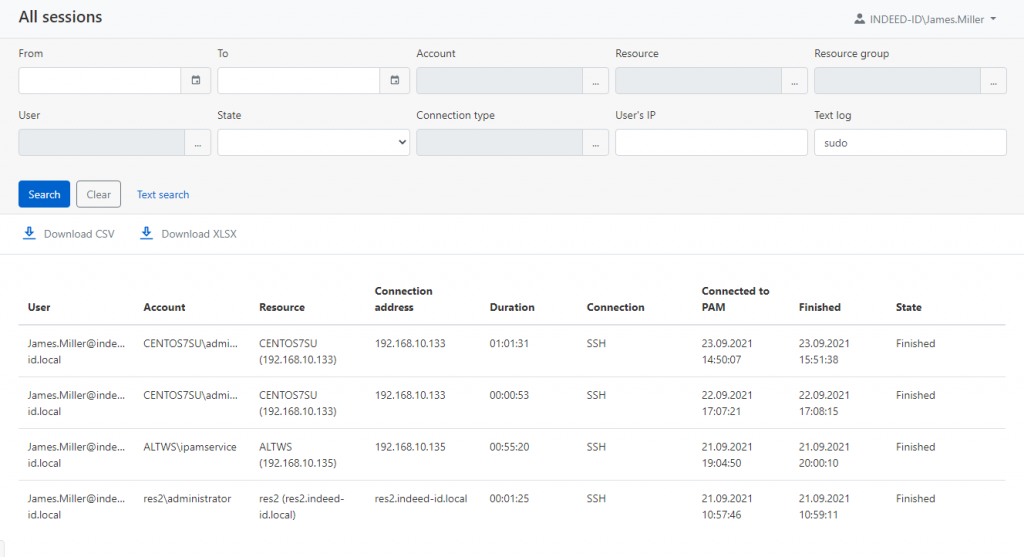
Text record search across all sessions
The updated text log search feature allows you to quickly find entered commands. The search is performed across the entire array of session records. This feature will help respond to potential threats and, in a timely manner, detect attempts to enter commands that are uncommon for most employees.
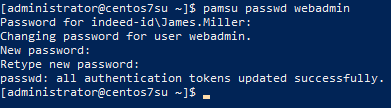
Own implementation of sudo
When using PAM, privileged users generally do not own the credentials. It makes *nix systems hard to administer, for example, in cases when a password for an account must be provided to elevate privileges (execute the sudo command). The new version of Axidian Privilege offers an alternative to sudo – the pamsu command, which allows you to safely elevate privileges in SSH sessions. In order to elevate privileges, a PAM user has to go through two-factor authentication on his or her own behalf. So, there is no need to disclose the privileged credentials to PAM users. The pamsu command can be enabled or disabled in PAM policies, and if necessary a PAM administrator can prohibit users from executing it.
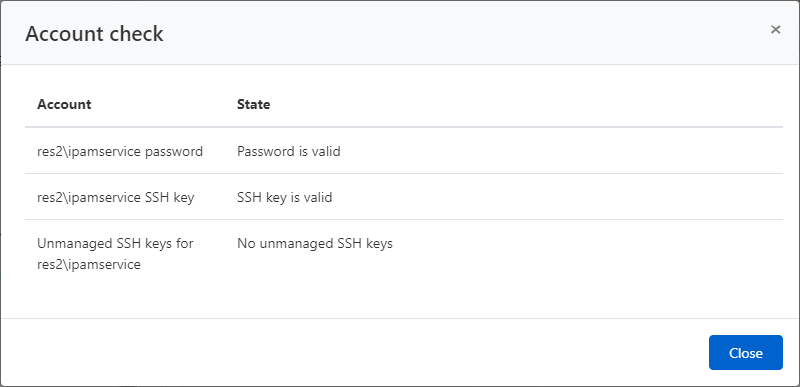
Automatic search for and removal of third-party SSH keys
The new version of Axidian Privilege offers better control over privileged accounts on *nix systems. The new feature automatically removes third-party SSH keys so that only keys generated by Axidian Privilege are used to access resources. The search for uncontrolled keys is a regularly performed process, just like the search for new accounts and password checking.
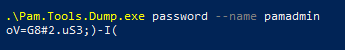
Emergency password retrieval from PAM
A mechanism has been developed for emergency access to passwords in the Axidian Privilege database in the “Red Button” scenario. It is implemented as a separate utility, which allows retrieving passwords of all or certain privileged accounts in case of an emergency involving a global PAM failure.